The “Internet of Things” without security = The “Internet of Threats”
– Stephane Nappo, Global Head Information Security, Groupe SEB
At Celtrino, we take data security very seriously. We implement several internal and external protocols to ensure none of the information in any of our systems gets into the wrong hands.
As part of our ever-improving data security practices, we have recently started to roll out Multi-Factor Authentication (MFA) across all levels of our business. If you use our PEPPOL Connect service or anything which requires you to log into a system which we control, chances are you’ll start to see MFA more and more often; so it’s important to understand both how it works and the benefits it brings with it.
What is MFA & how does it work?
Multi-Factor Authentication (MFA), is an authentication technique that requires a user to submit two or more verification factors in order to obtain access to a resource such as an application, an online account, or a VPN. A robust identity and access management (IAM) policy must include multi-factor authentication (MFA).
MFA is often called “Two Factor Authentication” (2FA), however this isnt strictly accurate as 2FA only uses two factors to verify a user’s identity. MFA can involve two of the factors or it can involve all three.
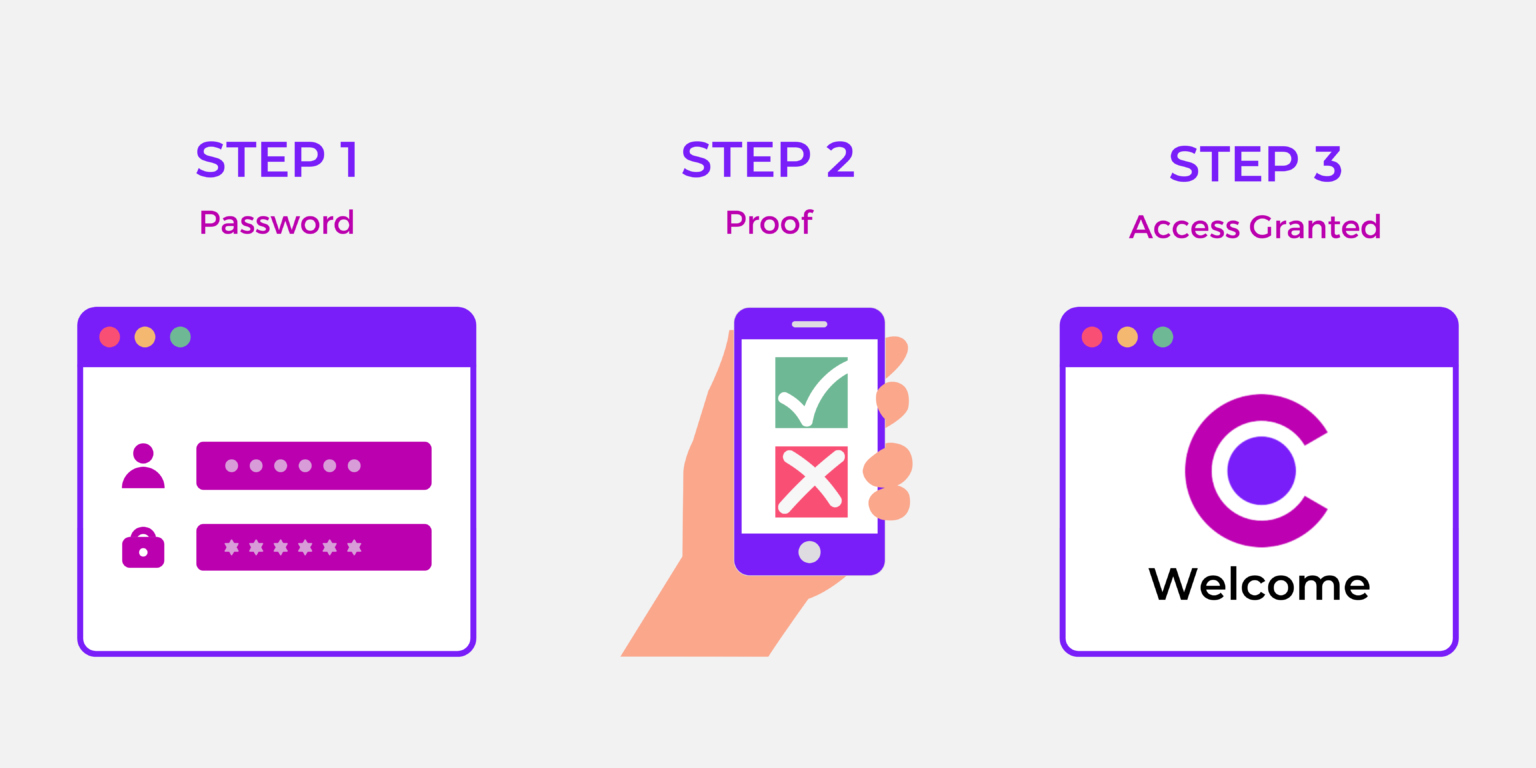
MFA works in three stages:
- Firstly, you are prompted to enter a username and password as you normally would
- Then, you will be required to prove your identity via an external medium, such as a one-time passcode (OTP) sent to you via email or text message
- Finally, if you have successfully completed the proofing process, you will be granted access to the system you were trying to log into.
Performing these distinct and logical steps will give Celtrino the guarantee you are who you claim to be and not a robot or cyber-criminal looking to infiltrate our systems. Additionally, you can rest easy knowing that thanks to this heightened verification, all your personal data is safer than ever.

Why is it important?
The key advantage of MFA is that it increases the security of your business by forcing users to identify themselves with more than just a username and password. Usernames and passwords, while vital, are subject to brute force assaults and can be stolen by third parties. Enforcing the usage of a multi-factor authentication (MFA) element such as a one-time passcode (OTP) increases your organisation’s trust in its ability to protect itself against data theft.
When you only require a single basic password to authenticate a user, you’re leaving an entry point open for attackers to walk through. The system often cannot detect whether it is the authorised user logging in or not, but when a second form of authentication is required, security is enhanced since the additional element is difficult for an attacker to search for or replicate.
Examples of MFA
MFA has three key pillars to how it can be implemented in a particular system:
- Something you know – This could involve the use of an additional password you can recall from memory or a 4-digit PIN you have memorised. Most banks offer this kind of MFA.
- Something you possess – This type of MFA includes items such as receiving an OTP to your email or phone, a key fob or even software certificates. We are implementing this type of authentication on many of our systems; both internal and external.
- Something you are – This is the most advanced kind of MFA, utilising things like Artificial Intelligence (AI), fingerprint recognition, and even biometric retina scanners. AI is a particularly exciting tool for MFA, as it can theoretically learn how you behave while logging into something and grant access based on complex calculations.
Take a look at how our new MFA has been integrated into some PEPPOL Connect accounts recently by watching the video below.
MFA is discussed from 00:20-00:40
The Celtrino Offering
One example of Celtrino MFA implementation can be seen in our PEPPOL Connect e-document portal. This portal allows suppliers and their buyers to exchange invoices, credit notes, purchase orders and other documents in a common format over the PEPPOL network.
We have over 30 years’ experience in providing EDI Invoicing solutions to our clients, so why not click the button below to Contact Us today to learn more about how we can assist you with all your e-Invoicing needs.